Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To remove access from an Azure resource, you remove a role assignment. This article describes how to remove roles assignments using the Azure portal, Azure PowerShell, Azure CLI, and REST API.
Prerequisites
To remove role assignments, you must have:
Microsoft.Authorization/roleAssignments/deletepermissions, such as Role Based Access Control Administrator
For the REST API, you must use the following version:
2015-07-01or later
For more information, see API versions of Azure RBAC REST APIs.
Azure portal
Follow these steps:
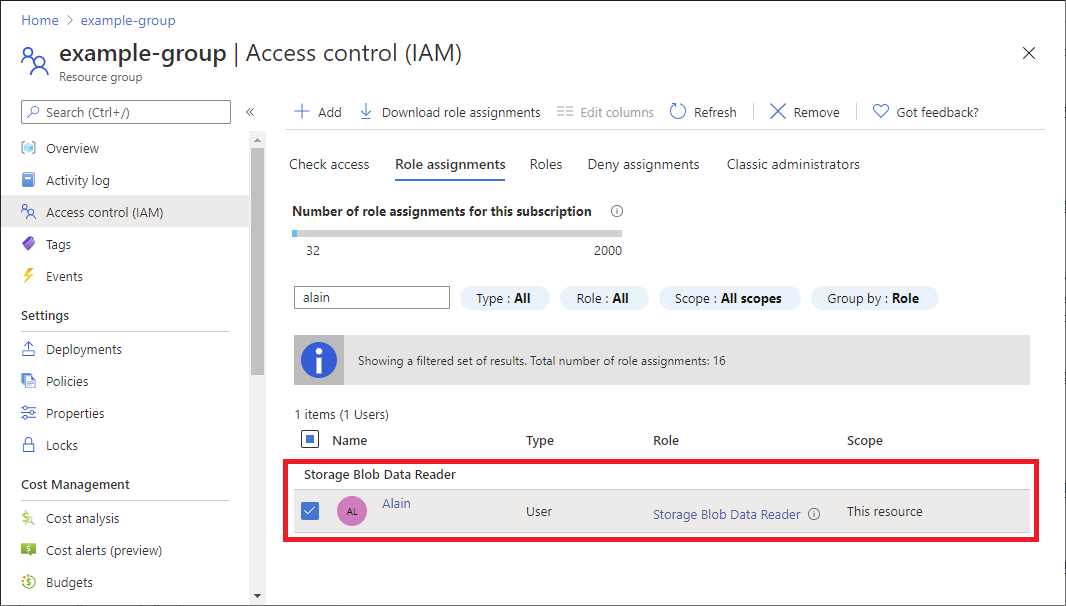
Open Access control (IAM) at a scope, such as management group, subscription, resource group, or resource, where you want to remove access.
Click the Role assignments tab to view all the role assignments at this scope.
In the list of role assignments, add a checkmark next to the security principal with the role assignment you want to remove.
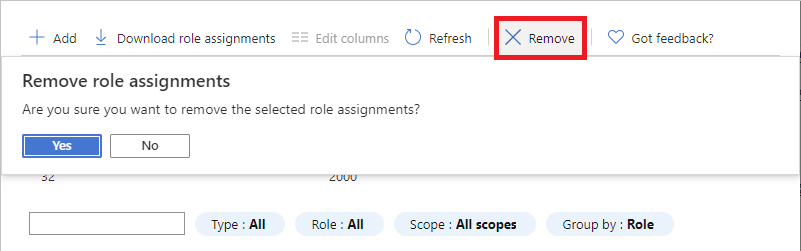
Click Remove.
In the remove role assignment message that appears, click Yes.
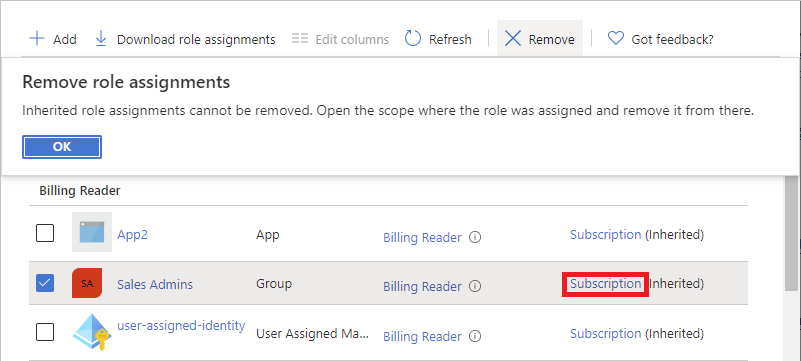
If you see a message that inherited role assignments cannot be removed, you are trying to remove a role assignment at a child scope. You should open Access control (IAM) at the scope where the role was assigned and try again. A quick way to open Access control (IAM) at the correct scope is to look at the Scope column and click the link next to (Inherited).
Azure PowerShell
In Azure PowerShell, you remove a role assignment by using Remove-AzRoleAssignment.
The following example removes the Virtual Machine Contributor role assignment from the patlong@contoso.com user on the pharma-sales resource group:
PS C:\> Remove-AzRoleAssignment -SignInName patlong@contoso.com `
-RoleDefinitionName "Virtual Machine Contributor" `
-ResourceGroupName pharma-sales
Removes the Reader role from the Ann Mack Team group with ID 22222222-2222-2222-2222-222222222222 at a subscription scope.
PS C:\> Remove-AzRoleAssignment -ObjectId 22222222-2222-2222-2222-222222222222 `
-RoleDefinitionName "Reader" `
-Scope "/subscriptions/00000000-0000-0000-0000-000000000000"
Removes the Billing Reader role from the alain@example.com user at the management group scope.
PS C:\> Remove-AzRoleAssignment -SignInName alain@example.com `
-RoleDefinitionName "Billing Reader" `
-Scope "/providers/Microsoft.Management/managementGroups/marketing-group"
Removes the User Access Administrator role with ID 18d7d88d-d35e-4fb5-a5c3-7773c20a72d9 from the principal with ID 33333333-3333-3333-3333-333333333333 at subscription scope with ID 00000000-0000-0000-0000-000000000000.
PS C:\> Remove-AzRoleAssignment -ObjectId 33333333-3333-3333-3333-333333333333 `
-RoleDefinitionId 18d7d88d-d35e-4fb5-a5c3-7773c20a72d9 `
-Scope /subscriptions/00000000-0000-0000-0000-000000000000
If you get the error message: "The provided information does not map to a role assignment", make sure that you also specify the -Scope or -ResourceGroupName parameters. For more information, see Troubleshoot Azure RBAC.
Azure CLI
In Azure CLI, you remove a role assignment by using az role assignment delete.
The following example removes the Virtual Machine Contributor role assignment from the patlong@contoso.com user on the pharma-sales resource group:
az role assignment delete --assignee "patlong@contoso.com" \
--role "Virtual Machine Contributor" \
--resource-group "pharma-sales"
Removes the Reader role from the Ann Mack Team group with ID 22222222-2222-2222-2222-222222222222 at a subscription scope.
az role assignment delete --assignee "22222222-2222-2222-2222-222222222222" \
--role "Reader" \
--scope "/subscriptions/00000000-0000-0000-0000-000000000000"
Removes the Billing Reader role from the alain@example.com user at the management group scope.
az role assignment delete --assignee "alain@example.com" \
--role "Billing Reader" \
--scope "/providers/Microsoft.Management/managementGroups/marketing-group"
REST API
In the REST API, you remove a role assignment by using Role Assignments - Delete.
Get the role assignment identifier (GUID). This identifier is returned when you first create the role assignment or you can get it by listing the role assignments.
Start with the following request:
DELETE https://management.chinacloudapi.cn/{scope}/providers/Microsoft.Authorization/roleAssignments/{roleAssignmentId}?api-version=2022-04-01Within the URI, replace {scope} with the scope for removing the role assignment.
Scope Type providers/Microsoft.Management/managementGroups/{groupId1}Management group subscriptions/{subscriptionId1}Subscription subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1Resource group subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1/providers/microsoft.web/sites/mysite1Resource Replace {roleAssignmentId} with the GUID identifier of the role assignment.
The following request removes the specified role assignment at subscription scope:
DELETE https://management.chinacloudapi.cn/subscriptions/{subscriptionId1}/providers/microsoft.authorization/roleassignments/{roleAssignmentId1}?api-version=2022-04-01The following shows an example of the output:
{ "properties": { "roleDefinitionId": "/subscriptions/{subscriptionId1}/providers/Microsoft.Authorization/roleDefinitions/a795c7a0-d4a2-40c1-ae25-d81f01202912", "principalId": "{objectId1}", "principalType": "User", "scope": "/subscriptions/{subscriptionId1}", "condition": null, "conditionVersion": null, "createdOn": "2022-05-06T23:55:24.5379478Z", "updatedOn": "2022-05-06T23:55:24.5379478Z", "createdBy": "{createdByObjectId1}", "updatedBy": "{updatedByObjectId1}", "delegatedManagedIdentityResourceId": null, "description": null }, "id": "/subscriptions/{subscriptionId1}/providers/Microsoft.Authorization/roleAssignments/{roleAssignmentId1}", "type": "Microsoft.Authorization/roleAssignments", "name": "{roleAssignmentId1}" }ARM template
There isn't a way to remove a role assignment using an Azure Resource Manager template (ARM template). To remove a role assignment, you must use other tools such as the Azure portal, Azure PowerShell, Azure CLI, or REST API.