Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
A Point-to-Site (P2S) VPN gateway connection lets you create a secure connection to your virtual network from an individual client computer. A P2S connection is established by starting it from the client computer. This solution is useful for telecommuters who want to connect to Azure virtual networks from a remote location, such as from home or a conference. P2S VPN is also a useful solution to use instead of site-to-site (S2S) VPN when you have only a few clients that need to connect to a virtual network. Point-to-site configurations require a route-based VPN type.
What protocol does P2S use?
Point-to-site VPN can use one of the following protocols:
OpenVPN® Protocol, an SSL/TLS based VPN protocol. A TLS VPN solution can penetrate firewalls, since most firewalls open TCP port 443 outbound, which TLS uses. OpenVPN can be used to connect from Android, Windows, Linux, and Mac devices (macOS versions 10.13 and above). Supported versions are TLS 1.2 and TLS 1.3 based on TLS handshake.
Secure Socket Tunneling Protocol (SSTP), a proprietary TLS-based VPN protocol. A TLS VPN solution can penetrate firewalls, since most firewalls open TCP port 443 outbound, which TLS uses. SSTP is only supported on Windows devices. Azure supports all versions of Windows that have SSTP and support TLS 1.2 (Windows 8.1 and later).
IKEv2 VPN, a standards-based IPsec VPN solution. IKEv2 VPN can be used to connect from Mac devices (macOS versions 10.11 and above).
How are P2S VPN clients authenticated?
Before Azure accepts a P2S VPN connection, the user has to be authenticated first. There are three authentication types that you can select when you configure your P2S gateway. The options are:
You can select multiple authentication types for your P2S gateway configuration. If you select multiple authentication types, the VPN client you use must be supported by at least one authentication type and corresponding tunnel type. For example, if you select "IKEv2 and OpenVPN" for tunnel types, and "Microsoft Entra ID and Radius" or "Microsoft Entra ID and Azure Certificate" for authentication type, Microsoft Entra ID will only use the OpenVPN tunnel type since it's not supported by IKEv2.
The following table shows authentication mechanisms that are compatible with selected tunnel types. Each mechanism requires corresponding VPN client software on the connecting device to be configured with the proper settings available in the VPN client profile configuration files.
| Tunnel Type | Authentication Mechanism |
|---|---|
| OpenVPN | Any subset of Microsoft Entra ID, Radius Auth and Azure Certificate |
| SSTP | Radius Auth/ Azure Certificate |
| IKEv2 | Radius Auth/ Azure Certificate |
| IKEv2 and OpenVPN | Radius Auth/ Azure Certificate/ Microsoft Entra ID and Radius Auth/ Microsoft Entra ID and Azure Certificate |
| IKEv2 and SSTP | Radius Auth/ Azure Certificate |
Certificate authentication
When you configure your P2S gateway for certificate authentication, you upload the trusted root certificate public key to the Azure gateway. You can use a root certificate that was generated using an Enterprise solution, or you can generate a self-signed certificate.
To authenticate, each client that connects must have an installed client certificate that's generated from the trusted root certificate. This is in addition to VPN client software. The validation of the client certificate is performed by the VPN gateway and happens during establishment of the P2S VPN connection.
Certificate authentication workflow
At a high level, you need to perform the following steps to configure Certificate authentication:
- Enable Certificate authentication on the P2S gateway, along with the additional required settings (client address pool, etc.), and upload the root CA public key information.
- Generate and download VPN client profile configuration files (profile configuration package).
- Install the client certificate on each connecting client computer.
- Configure the VPN client on the client computer using the settings found in the VPN profile configuration package.
- Connect.
Microsoft Entra ID authentication
You can configure your P2S gateway to allow VPN users to authenticate using Microsoft Entra ID credentials. With Microsoft Entra ID authentication, you can use Microsoft Entra Conditional Access and multifactor authentication (MFA) features for VPN. Microsoft Entra ID authentication is supported only for the OpenVPN protocol. To authenticate and connect, clients must use the Azure VPN Client.
VPN Gateway now supports a new Microsoft-registered App ID and corresponding Audience values for the latest versions of the Azure VPN Client. When you configure a P2S VPN gateway using the new Audience values, you skip the previously required Azure VPN Client app manual registration process for your Microsoft Entra tenant. The App ID is already created and your tenant is automatically able to use it with no extra registration steps. This process is more secure than manually registering the Azure VPN Client because you don't need to authorize the app or assign permissions via the Cloud App Administrator role. To better understand the difference between the types of application objects, see How and why applications are added to Microsoft Entra ID.
- If your P2S User VPN gateway is configured using the Audience values for the manually configured Azure VPN Client app, you can easily change the gateway and client settings to take advantage of the new Microsoft-registered App ID. If you want Linux clients to connect, you must update the P2S gateway with the new Audience value. The Azure VPN Client for Linux isn't backward compatible with the older Audience values.
- If you want to create or modify a custom Audience value, see Create a custom audience app ID for P2S VPN.
- If you want to configure or restrict access to P2S based on users and groups, see Scenario: Configure P2S VPN access based on users and groups.
Considerations
A P2S VPN gateway can only support one Audience value. It can't support multiple Audience values simultaneously.
The Azure VPN Client for Linux isn't backward compatible with P2S gateways configured to use the older Audience values that align with the manually registered app. However, the Azure VPN Client for Linux does support Custom Audience values.
-
While it's possible that the Azure VPN Client for Linux might work on other Linux distributions and releases, the Azure VPN Client for Linux is only supported on the following releases:
- Ubuntu 20.04
- Ubuntu 22.04
The latest versions of the Azure VPN Clients for macOS and Windows are backward compatible with P2S gateways configured to use the older Audience values that align with the manually registered app. These clients also support Custom Audience values.
Azure VPN Client Audience values
The following table shows the versions of the Azure VPN Client that are supported for each App ID and the corresponding available Audience values.
| App ID | Supported Audience values | Supported clients |
|---|---|---|
| Microsoft-registered | c632b3df-fb67-4d84-bdcf-b95ad541b5c8 |
- Linux - Windows |
| Manually registered | 49f817b6-84ae-4cc0-928c-73f27289b3aa |
Windows |
| Custom | <custom-app-id> |
- Linux - Windows |
Microsoft Entra ID authentication workflow
At a high level, you need to perform the following steps to configure Microsoft Entra ID authentication:
- If using manual app registration, perform the necessary steps on the Microsoft Entra tenant.
- Enable Microsoft Entra ID authentication on the P2S gateway, along with the additional required settings (client address pool, etc.).
- Generate and download VPN client profile configuration files (profile configuration package).
- Download, install, and configure the Azure VPN Client on the client computer.
- Connect.
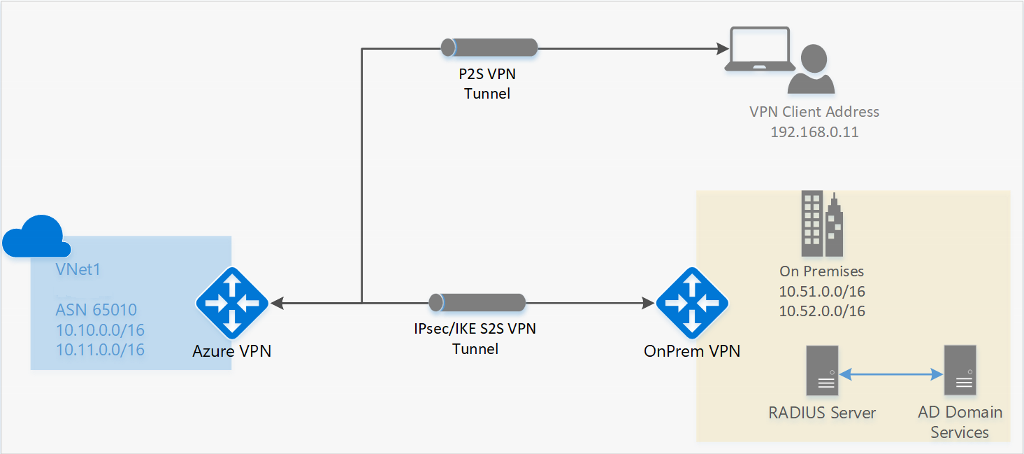
RADIUS - Active Directory (AD) Domain Server authentication
AD Domain authentication allows users to connect to Azure using their organization domain credentials. It requires a RADIUS server that integrates with the AD server. Organizations can also use their existing RADIUS deployment.
The RADIUS server could be deployed on-premises or in your Azure virtual network. During authentication, the Azure VPN Gateway acts as a pass through and forwards authentication messages back and forth between the RADIUS server and the connecting device. So Gateway reachability to the RADIUS server is important. If the RADIUS server is present on-premises, then a VPN S2S connection from Azure to the on-premises site is required for reachability.
The RADIUS server can also integrate with AD certificate services. This lets you use the RADIUS server and your enterprise certificate deployment for P2S certificate authentication as an alternative to the Azure certificate authentication. The advantage is that you don’t need to upload root certificates and revoked certificates to Azure.
A RADIUS server can also integrate with other external identity systems. This opens up plenty of authentication options for P2S VPN, including multi-factor options.
For P2S gateway configuration steps, see Configure P2S - RADIUS.
What are the client configuration requirements?
The client configuration requirements vary, based on the VPN client that you use, the authentication type, and the protocol. The following table shows the available clients and the corresponding articles for each configuration.
| Authentication method | Tunnel type | Client OS | VPN client |
|---|---|---|---|
| Certificate | |||
| IKEv2, SSTP | Windows | Native VPN client | |
| IKEv2 | macOS | Native VPN client | |
| IKEv2 | Linux | strongSwan | |
| OpenVPN | Windows | Azure VPN client OpenVPN client version 2.x OpenVPN client version 3.x |
|
| OpenVPN | macOS | OpenVPN client | |
| OpenVPN | Linux | Azure VPN Client OpenVPN client |
|
| Microsoft Entra ID | |||
| OpenVPN | Windows | Azure VPN client | |
| OpenVPN | Linux | Azure VPN Client |
What versions of the Azure VPN Client are available?
For information about available Azure VPN Client versions, release dates, and what's new in each release, see Azure VPN Client versions.
Which gateway SKUs support P2S VPN?
The following table shows gateway SKUs by tunnel, connection, and throughput. For more information, see About gateway SKUs.
| VPN Gateway Generation |
SKU | S2S/VNet-to-VNet Tunnels |
P2S SSTP Connections |
P2S IKEv2/OpenVPN Connections |
Aggregate Throughput Benchmark |
BGP | Zone-redundant | Supported Number of VMs in the Virtual Network |
|---|---|---|---|---|---|---|---|---|
| Generation1 | Basic | Max. 10 | Max. 128 | Not Supported | 100 Mbps | Not Supported | No | 200 |
| Generation1 | VpnGw1 | Max. 30 | Max. 128 | Max. 250 | 650 Mbps | Supported | No | 450 |
| Generation1 | VpnGw2 | Max. 30 | Max. 128 | Max. 500 | 1 Gbps | Supported | No | 1300 |
| Generation1 | VpnGw3 | Max. 30 | Max. 128 | Max. 1000 | 1.25 Gbps | Supported | No | 4000 |
| Generation1 | VpnGw1AZ | Max. 30 | Max. 128 | Max. 250 | 650 Mbps | Supported | Yes | 1000 |
| Generation1 | VpnGw2AZ | Max. 30 | Max. 128 | Max. 500 | 1 Gbps | Supported | Yes | 2000 |
| Generation1 | VpnGw3AZ | Max. 30 | Max. 128 | Max. 1000 | 1.25 Gbps | Supported | Yes | 5000 |
| Generation2 | VpnGw2 | Max. 30 | Max. 128 | Max. 500 | 1.25 Gbps | Supported | No | 685 |
| Generation2 | VpnGw3 | Max. 30 | Max. 128 | Max. 1000 | 2.5 Gbps | Supported | No | 2240 |
| Generation2 | VpnGw4 | Max. 100* | Max. 128 | Max. 5000 | 5 Gbps | Supported | No | 5300 |
| Generation2 | VpnGw5 | Max. 100* | Max. 128 | Max. 10000 | 10 Gbps | Supported | No | 6700 |
| Generation2 | VpnGw2AZ | Max. 30 | Max. 128 | Max. 500 | 1.25 Gbps | Supported | Yes | 2000 |
| Generation2 | VpnGw3AZ | Max. 30 | Max. 128 | Max. 1000 | 2.5 Gbps | Supported | Yes | 3300 |
| Generation2 | VpnGw4AZ | Max. 100* | Max. 128 | Max. 5000 | 5 Gbps | Supported | Yes | 4400 |
| Generation2 | VpnGw5AZ | Max. 100* | Max. 128 | Max. 10000 | 10 Gbps | Supported | Yes | 9000 |
Note
The Basic SKU has limitations and does not support IKEv2, IPv6, or RADIUS authentication. For more information, see VPN Gateway settings.
What IKE/IPsec policies are configured on VPN gateways for P2S?
The tables in this section show the values for the default policies. However, they don't reflect the available supported values for custom policies. For custom policies, see the Accepted values listed in the New-AzVpnClientIpsecParameter PowerShell cmdlet.
IKEv2
| Cipher | Integrity | PRF | DH Group |
|---|---|---|---|
| GCM_AES256 | GCM_AES256 | SHA384 | GROUP_24 |
| GCM_AES256 | GCM_AES256 | SHA384 | GROUP_14 |
| GCM_AES256 | GCM_AES256 | SHA384 | GROUP_ECP384 |
| GCM_AES256 | GCM_AES256 | SHA384 | GROUP_ECP256 |
| GCM_AES256 | GCM_AES256 | SHA256 | GROUP_24 |
| GCM_AES256 | GCM_AES256 | SHA256 | GROUP_14 |
| GCM_AES256 | GCM_AES256 | SHA256 | GROUP_ECP384 |
| GCM_AES256 | GCM_AES256 | SHA256 | GROUP_ECP256 |
| AES256 | SHA384 | SHA384 | GROUP_24 |
| AES256 | SHA384 | SHA384 | GROUP_14 |
| AES256 | SHA384 | SHA384 | GROUP_ECP384 |
| AES256 | SHA384 | SHA384 | GROUP_ECP256 |
| AES256 | SHA256 | SHA256 | GROUP_24 |
| AES256 | SHA256 | SHA256 | GROUP_14 |
| AES256 | SHA256 | SHA256 | GROUP_ECP384 |
| AES256 | SHA256 | SHA256 | GROUP_ECP256 |
| AES256 | SHA256 | SHA256 | GROUP_2 |
IPsec
| Cipher | Integrity | PFS Group |
|---|---|---|
| GCM_AES256 | GCM_AES256 | GROUP_NONE |
| GCM_AES256 | GCM_AES256 | GROUP_24 |
| GCM_AES256 | GCM_AES256 | GROUP_14 |
| GCM_AES256 | GCM_AES256 | GROUP_ECP384 |
| GCM_AES256 | GCM_AES256 | GROUP_ECP256 |
| AES256 | SHA256 | GROUP_NONE |
| AES256 | SHA256 | GROUP_24 |
| AES256 | SHA256 | GROUP_14 |
| AES256 | SHA256 | GROUP_ECP384 |
| AES256 | SHA256 | GROUP_ECP256 |
| AES256 | SHA1 | GROUP_NONE |
What TLS policies are configured on VPN gateways for P2S?
TLS
| Policies |
|---|
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 |
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 |
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 |
| **TLS_AES_256_GCM_SHA384 |
| **TLS_AES_128_GCM_SHA256 |
**Only supported on TLS1.3 with OpenVPN
How do I configure a P2S connection?
A P2S configuration requires quite a few specific steps. The following articles contain the steps to walk you through common P2S configuration steps.
To remove the configuration of a P2S connection
You can remove the configuration of a connection by using PowerShell or CLI. For examples, see the FAQ.
How does P2S routing work?
See the following articles:
FAQs
There are multiple FAQ entries for point-to-site. See the VPN Gateway FAQ, paying particular attention to the Certificate authentication and RADIUS sections, as appropriate.
Next Steps
- Configure a P2S connection - Azure certificate authentication
- Configure a P2S connection - Microsoft Entra ID authentication
"OpenVPN" is a trademark of OpenVPN Inc.