Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Defender for Cloud's Defender for Servers Plan offers the just-in-time machine access feature. Just-in-time protects your resources from threat actors actively hunting for machines with open management ports, such as Remote Desktop Protocol (RDP) or Secure Shell (SSH). All machines are potential targets for attacks. Once compromised, a machine can serve as an entry point to further attack resources in the environment.
To reduce attack surfaces, minimize open ports, especially management ports. However, legitimate users also need these ports, making it impractical to keep them closed.
Defender for Cloud's just-in-time machine access feature locks down inbound traffic to your virtual machines (VMs), reducing exposure to attacks while ensuring easy access when needed.
Just-in-time access and network resources
Azure
In Azure, enable just-in-time access to block inbound traffic on specific ports.
- Defender for Cloud ensures "deny all inbound traffic" rules exist for your selected ports in the network security group (NSG) and Azure Firewall rules.
- These rules restrict access to your Azure VMs' management ports and defend them from attack.
- If other rules already exist for the selected ports, those existing rules take priority over the new "deny all inbound traffic" rules.
- If no existing rules are on the selected ports, the new rules take top priority in the NSG and Azure Firewall.
Identify VMs for just-in-time access
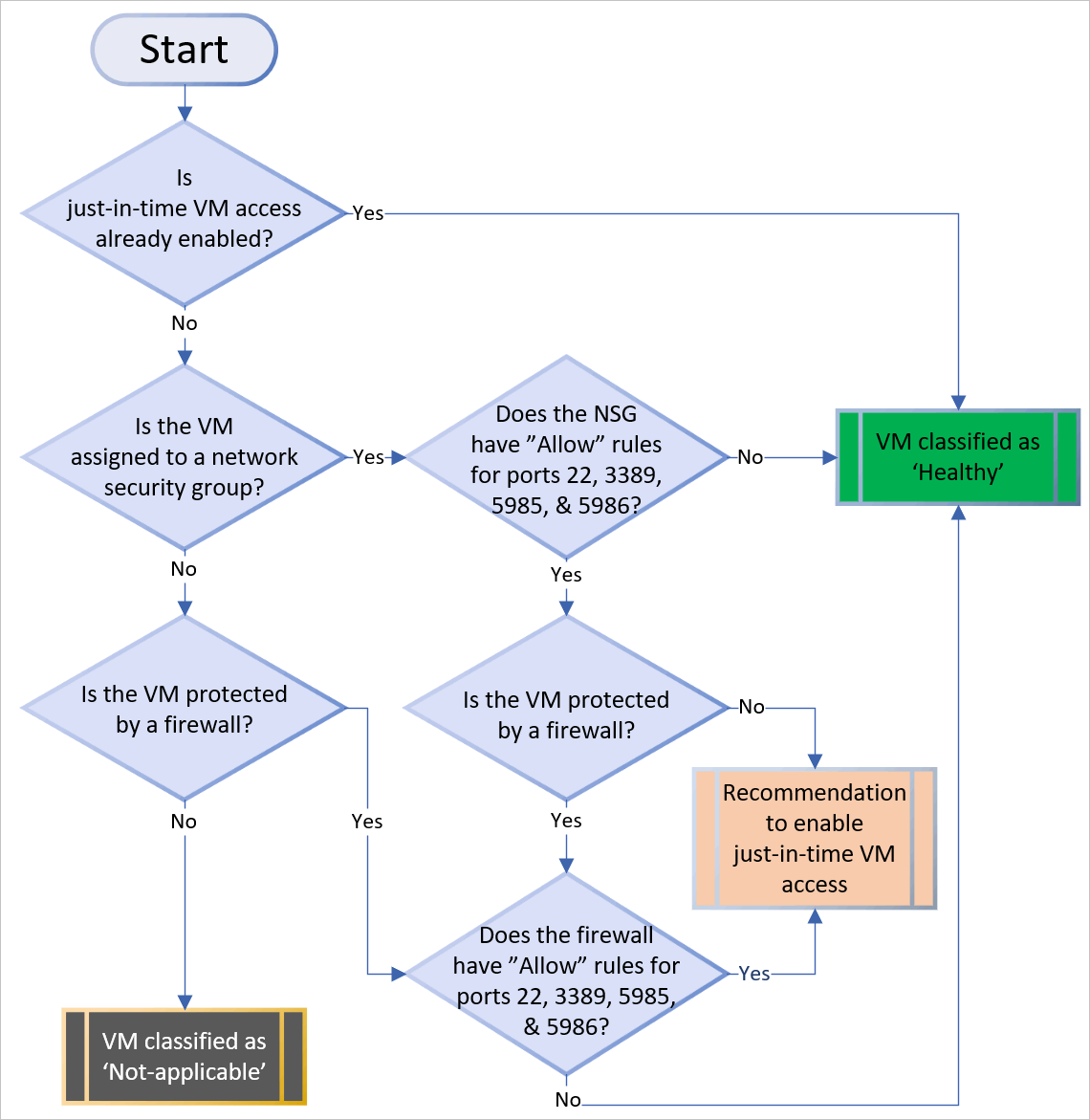
The following diagram shows the logic that Defender for Servers applies when deciding how to categorize your supported VMs:
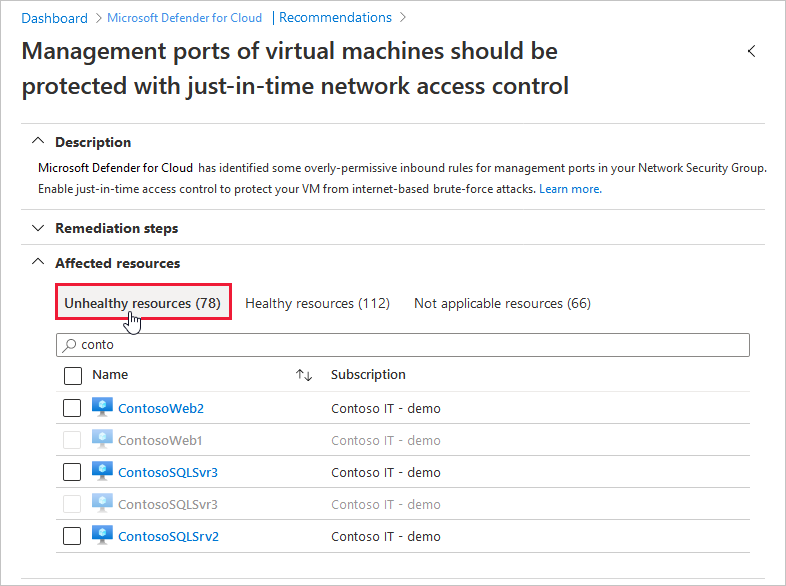
When Defender for Cloud finds a machine that can benefit from just-in-time access, it adds that machine to the recommendation's Unhealthy resources tab.