Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure Policy is a free service in Azure to create, assign, and manage policies that enforce rules and effects to ensure your resources stay compliant with your corporate standards and service level agreements. Use these policies to audit Web PubSub resources for compliance.
This article describes the built-in policies for Azure Web PubSub Service.
Built-in policy definitions
The following table contains an index of Azure Policy built-in policy definitions for Azure Web PubSub. For Azure Policy built-ins for other services, see Azure Policy built-in definitions.
The name of each built-in policy definition links to the policy definition in the Azure portal. Use the link in the Version column to view the source on the Azure Policy GitHub repo.
| Name (Azure portal) |
Description | Effect(s) | Version (GitHub) |
|---|---|---|---|
| Azure Web PubSub Service should disable public network access | Disabling public network access improves security by ensuring that Azure Web PubSub service isn't exposed on the public internet. Creating private endpoints can limit exposure of Azure Web PubSub service. Learn more at: https://aka.ms/awps/networkacls. | Audit, Deny, Disabled | 1.0.0 |
| Azure Web PubSub Service should use a SKU that supports private link | With supported SKU, Azure Private Link lets you connect your virtual network to Azure services without a public IP address at the source or destination. The Private Link platform handles the connectivity between the consumer and services over the Azure backbone network. By mapping private endpoints to Azure Web PubSub service, you can reduce data leakage risks. Learn more about private links at: https://aka.ms/awps/privatelink. | Audit, Deny, Disabled | 1.0.0 |
| Configure Azure Web PubSub Service to disable public network access | Disable public network access for your Azure Web PubSub resource so that it's not accessible over the public internet. This can reduce data leakage risks. Learn more at: https://aka.ms/awps/networkacls. | Modify, Disabled | 1.0.0 |
| Configure Azure Web PubSub Service to use private DNS zones | Use private DNS zones to override the DNS resolution for a private endpoint. A private DNS zone links to your virtual network to resolve to Azure Web PubSub service. Learn more at: https://aka.ms/awps/privatelink. | DeployIfNotExists, Disabled | 1.0.0 |
| Configure Azure Web PubSub Service with private endpoints | Private endpoints connect your virtual networks to Azure services without a public IP address at the source or destination. By mapping private endpoints to Azure Web PubSub service, you can reduce data leakage risks. Learn more about private links at: https://aka.ms/awps/privatelink. | DeployIfNotExists, Disabled | 1.0.0 |
Assign policy definitions
When assigning a policy definition:
- You can assign policy definitions using the Azure portal, Azure CLI, a Resource Manager template, or the Azure Policy SDKs.
- Policy assignments can be scoped to a resource group, a subscription, or an Azure management group.
- You can enable or disable policy enforcement at any time.
- Web PubSub policy assignments apply to existing and new Web PubSub resources within the scope.
Note
After you assign or update a policy, it takes some time for the assignment to be applied to resources in the defined scope. See information about policy evaluation triggers.
Review policy compliance
Access compliance information generated by your policy assignments using the Azure portal, Azure command-line tools, or the Azure Policy SDKs. For details, see Get compliance data of Azure resources.
When a resource is non-compliant, there are many possible reasons. To determine the reason or to find the change responsible, see Determine non-compliance.
Policy compliance in the portal:
- Open the Azure portal and search for Policy.
- Select Policy.
- Select Compliance.
- Use the filters to display by Scope, Type or Compliance state. Use search list by name or
ID.
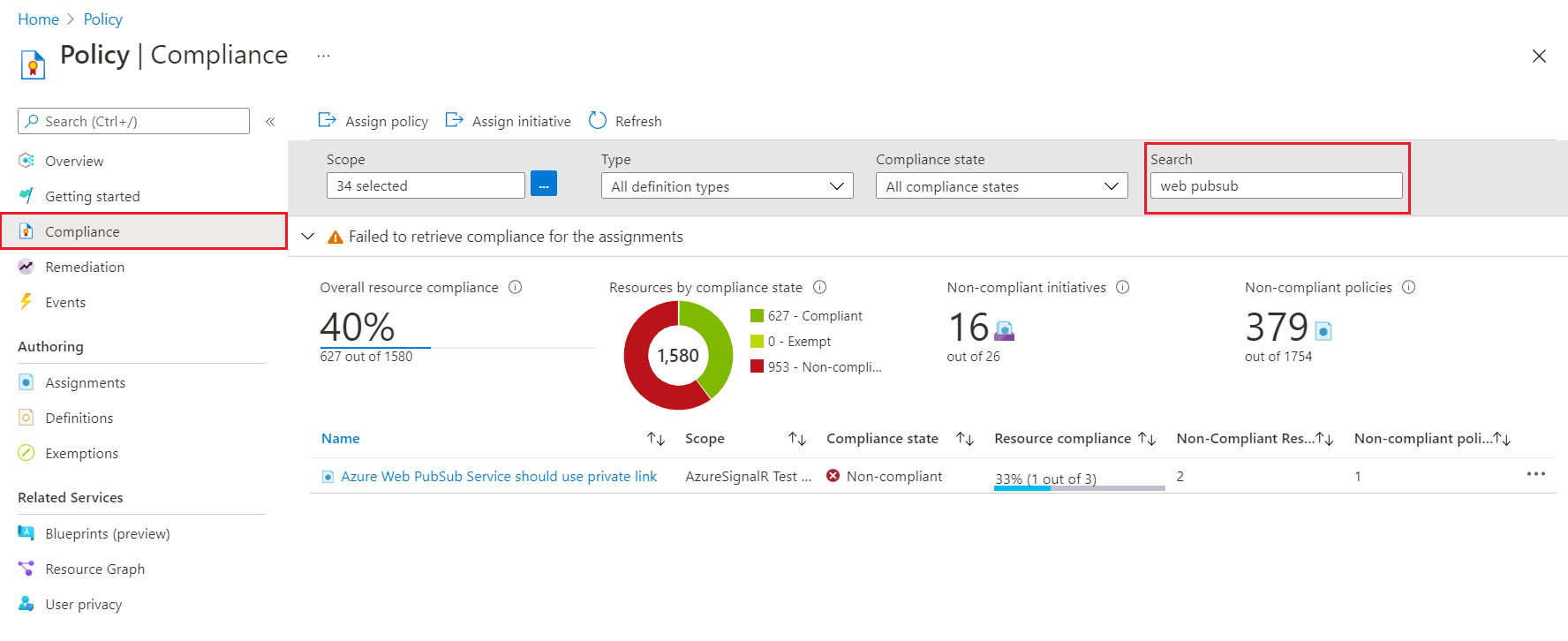
- Select a policy to review aggregate compliance details and events.
- Select a specific Web PubSub for resource compliance.
Policy compliance in the Azure CLI
You can use the Azure CLI to get compliance data. Use the az policy assignment list command to get the policy IDs of the Azure Web PubSub Service policies that are applied:
az policy assignment list --query "[?contains(displayName,'Web PubSub')].{name:displayName, ID:id}" --output table
Example output:
Name ID
------------------------------------------------------------------------------------- --------------------------------------------------------------------------------------------------------------------------------
[Preview]: Azure Web PubSub Service should use private links /subscriptions/<subscriptionId>/resourceGroups/<resourceGroup>/providers/Microsoft.Authorization/policyAssignments/<assignmentId>
Run the az policy state list command to return the JSON-formatted compliance state for all resources under a specific resource group:
az policy state list --g <resourceGroup>
Run the az policy state list command to return the JSON-formatted compliance state of a specific Web PubSub resource:
az policy state list \
--resource /subscriptions/<subscriptionId>/resourceGroups/<resourceGroup>/providers/Microsoft.SignalRService/WebPubSub/<resourceName> \
--namespace Microsoft.SignalRService \
--resource-group <resourceGroup>
Next steps
Learn more about Azure Policy definitions and effects
Create a custom policy definition
Learn more about governance capabilities in Azure